Cyber Security Solution
Deceptions & Traps
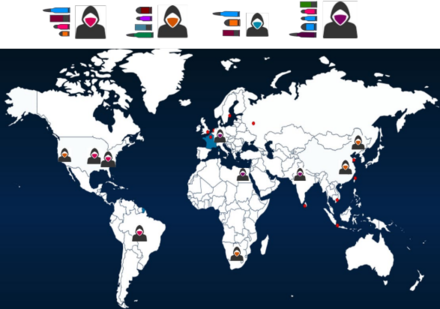
Creating digital replicas of IoT/IT devices and exposing them to the internet, enabling real-time monitoring of : Individuals attempting to attack or scan the system, New and unknown types of attacks targeting specific devices and services, Specific groups targeting particular organizations with their attacks.